
On 29 March, Palo Alto Networks, a global leader in cybersecurity has finally revealed the research report on the State of Cybersecurity through a virtual media briefing. The report covers on the ASEAN countries which include Malaysia, Indonesia, Thailand, Singapore, and the Philippines.
The State of Cybersecurity research was completed in November 2021 with participation from 100 information technology (IT) executives and senior business leaders from each country. In the report, Palo Alto Networks has highlighted 3 major key findings on Malaysia cybersecurity.
3 Key Findings Based On Malaysia Statistics
1.Cybersecurity Becomes A Top Priority In Businesses
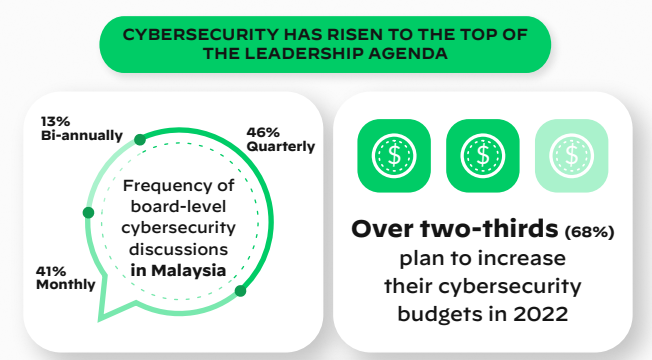
Many ASEAN businesses are now paying more intensive attention to their company’s cybersecurity protection to avoid cyberattacks. Specifically in Malaysia, the discussions on cybersecurity issues become the top priority at the board level with 46% of organizations doing it every quarter, 41% every month, and 13% biannually. Ian Lim, the Field Chief Security Officer of Palo Alto Networks, agrees that business leaders need to sit up and discuss the company’s cybersecurity.
The pandemic has served as a catalyst for ASEAN business leaders to sit up and pay greater attention to their cybersecurity defence measures — many are recognising the deep impact it can have on their business continuity. To manage today’s remote workforce in a digital-first environment, cybersecurity must be integrated horizontally across all facets of the business and considered as part of every corporate action.
Ian Lim, Field Chief Security Officer, Palo Alto Networks.
2. New Cybersecurity Challenges In Today’s Remote Work
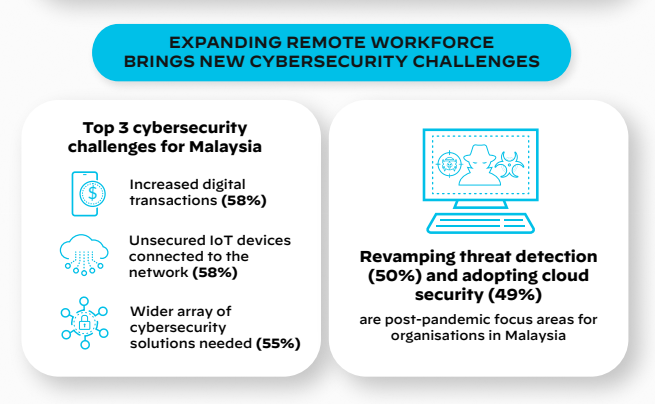
Now it becomes a norm where most people are working remotely, could be anywhere, and everywhere as long as the work is done. Due to this new working environment, we have to accept the fact that new cybersecurity challenges will come our way. For Malaysia cybersecurity, an enormous number of businesses have experienced a rise in cyberattacks in 2021. Among the new cybersecurity risks that were faced by the businesses are:
- the increase in digital transactions with suppliers and other third parties with 58%
- unmonitored and unsecured IoT devices connected to the corporate network with 58%
- the need to procure a wider array of cybersecurity solutions to protect themselves from cyberthreats with 55%
3. Develop cybersecurity Plans For Post-COVID World
Working remotely has resulted in many people using digital technologies. Therefore, there are a few strategies that should be taken into consideration to keep businesses stay protected from cyber threats. As in Malaysia, the two important measures that need to be implemented by organizations are the adoption of Revamping Threat Detection and Correlation systems and cloud security, followed by securing IoT/OT, identity and access management, and Secure Access Service Edge (SASE) strategy.
As said by Suk Hua Lim, the Country Manager of Palo Alto Networks Malaysia, she mentioned that it is crucial for Malaysian organizations to execute an effective cybersecurity plan at this time.
In order to effectively partake in Malaysia’s journey of digital transformation, it is imperative for organisations to design and implement an effective and full-proof cybersecurity strategy. It is inspiring to see that Malaysian organisations have confidence in their cybersecurity measures and that they are highly aware of taking the right decisions in protecting the nation from cyber disruptions.
Suk Hua Lim, Country Manager, Palo Alto Networks, Malaysia.
Recommendations For Businesses To Stay Ahead Of Cybersecurity Threats
- Run a cybersecurity assessment to understand, control, and reduce risks. This is to help organizations to identify what action should be taken for any threats.
- Adopt a Zero Trust framework to address the cybersecurity threats of today and design architecture with an “assume-breach” mindset. Deploy technology to continuously validate the legitimacy of digital interactions and establish rapid response capabilities to quickly address the early signs of a breach.
- Choose a partner, not a product. A good cybersecurity partner can provide the latest threat intelligence and offer practical advice on how to build a cyber-resilient architecture across all environments.
All in all, cyberattacks are a nightmare for every company in the whole world. That is why it is important for Malaysia organization to have a competent cybersecurity partner to assist with anything related to cybersecurity. For more information, kindly visit www.paloaltonetworks.com.










